❑Security related conversations - when speaking with Security Professionals about how to provide the necessary protection levels and access rights for their business information - are very interesting because they always have lots of opinions (e.g., options) on how best to provide the appropriate level of Security.
•Everyone has a different view of how secure they should make their system (e.g., safe but useable, totally "locked down").
•They know that a high level of security usually means that Employees will experience a lot of security related inconvenience.
•With MKMS Security and Access Management, it does not have to be that way!
❑All it takes is a little bit of planning.
•Decide on what information does - and does not - need intensive security protection.
•Identify the system entries that will enable your security protection plan.
•This security protection plan may require that system entries will include:
✓Setting up your security levels by establishing Security Groups.
✓Entering your individual Employees and identifying their Security Group assignment.
✓Entering User Name and Passwords so authorized Employees can Login.
✓Fine tuning who can see what, set what, and do what, using User Access Rights.
✓Adopt of the UL® Requirements for Password Security to maintain Passwords, and also to Login and Log out.
•When completed, your Users will rarely be aware of the underlying protections that have been put into place.
•UL® Requirements: As part of properly implementing the Third Edition UL® 1981 Standard, specifically for compliance with section 6.2 Sign-on Security and 6.3 (1-7) Five Security Levels of the Third Edition UL® 1981 Standard:
•6.2.1 - The Employee's Password (i.e., Passcode) shall consist of the following:
a)A Username of at least six (6) characters
b)A Password which shall consist of a minimum of six alpha-numeric characters with at least one alpha and one numeric character
6.2.3 - Any modification made to the database shall be logged with a unique personal identification (Employee ID) belonging to the person performing the modification).
i.To comply with 6.2.3 of theThird Edition UL® 1981 Standard, the Audit box must always be Checked for All Form Names when User Access Rights are assigned to any Employee or Employee Group
ii.Users cannot turn auditing off when the UL® Version is Registered (i.e., Active).
iii.In the User Access Rights and the Employee Groups Forms - when the UL® Version is Active -, the Audit option box will always be Checked on all Form Names.
iv.No User will be able to remove that Check Mark.
6.2.6 - The automation system shall prevent:
a)Repeated passwords, used within the last six changes;
b)Passwords that are a derivative of the user name(s); and
▪[e.g., Password cannot contain 50% of a Username so a User "Stacy" cannot have a Password of "STA3841"]
c)Passwords that are simply letters or numbers in order (e.g.: abcd, 1234, etc.).
▪[e.g., any type of sequence is prohibited such as 'ab', '34', '89', 'xy']
6.3 (1-7) - A minimum of Five Security Levels must be defined and the appropriate one assigned to each specific Employee based on that Employee's Need for Access.
➢Important Note: A few words about how to deal with a departing Employee:
✓If you need to remove an Employee from the system (due to termination, death, transfer, etc.), and that Employee has ever been assigned to any record (e.g., an Invoice, a Work Order, as an Operator handling Alarm Activity) within MKMS:
▪Do not delete that Employee's record in the Employee Form (they are part of the transactional history of your Company).
▪Instead, enter an Employment Period Ends Date on the Personal tab of the Employee Form.
▪If that Employee had system access to Login as a User, delete those records from the Add/Delete Users Form so they can no longer access the system.
❑Overview of Security and Access Management steps:
1.Define Employee Groups - this allows you to grant, to any employee assigned to that group, specified Forms and the rights to create, read, update, and/or delete the information on those Forms.
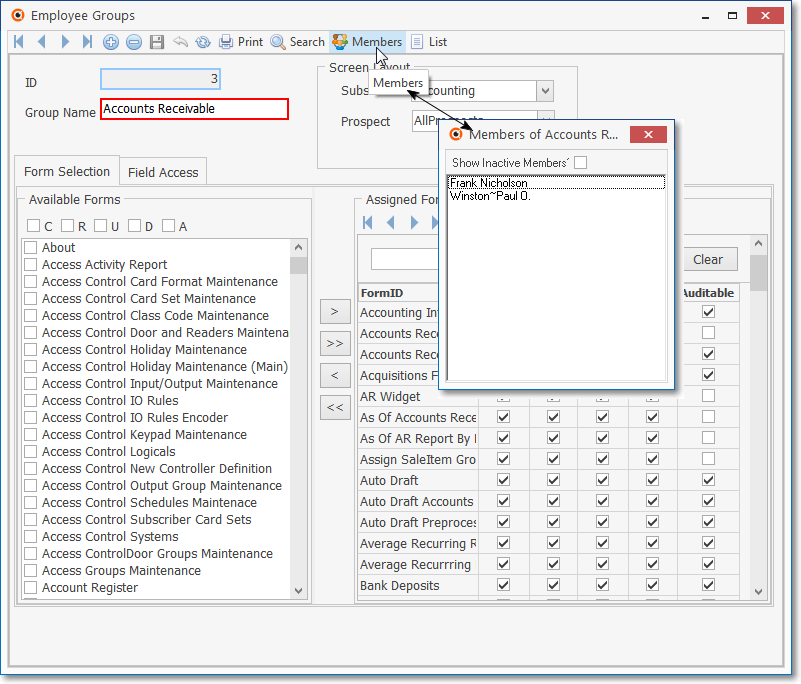
Employee Groups Form with Members data displayed
2.Enter your Employees.
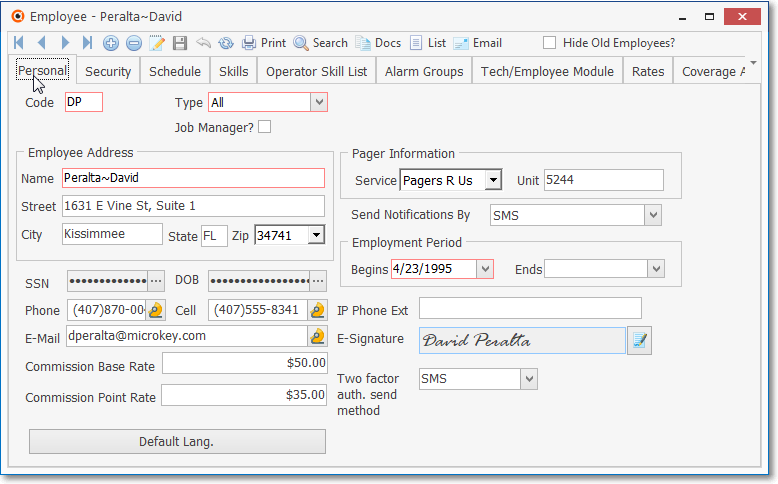
Employee Form - Personal tab
3.Using the Security tab on the Employees Form, assign each Employee to an Employee Group and turn on any of the additional rights - offered in this tab - that they must have to do their job.
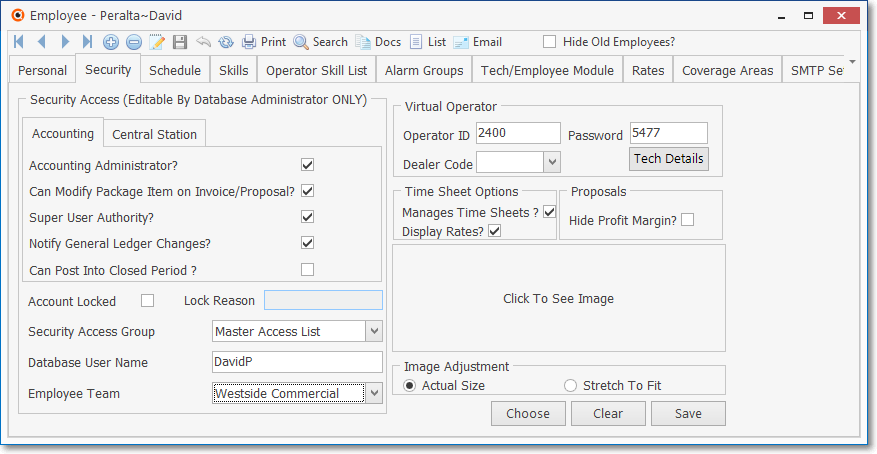
Employee Form - Security tab
4.Add these Employees to the system's Users file where you will assign them their Log In User Name and Password.
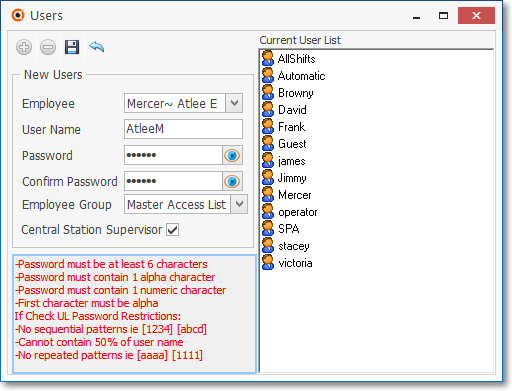
Add/Update Users Form
5.In the User Options Form on its Company Options tab, set the number of days before their Password Expires - thereby forcing them to periodically re-set it using the Change Passwords Form.
✓Passwords Expire? - Check this box if you want Employees to be required to periodically change their Password.
▪Reminder for Third Edition UL® 1981 Standard Users, this is Mandatory Requirement.
oPasswords must be changed at least every 90 Days.
oPasswords must be a minimum length of 6 alpha-numeric characters.
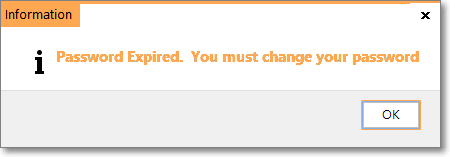
oUpon expiration, a Warning message is displayed which requires the User to immediately change their Password before continuing.
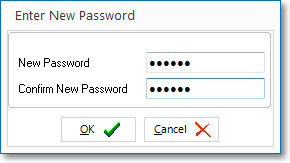
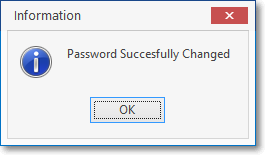
oOnce the new Password is entered, a confirmation message will be displayed.
❑Next, go to Employee Groups.